The primary purpose of a Vulnerability Assessment Report is to identify threats risks and vulnerabilities necessary to achieve the enterprise-wide security need. Risks of a threat-vulnerability pairing can be evaluated individually for Availability Integrity and Confidentiality AIC of the asset.

Risk Management Cybersecurity Strategy Risk Management Risk Management Strategies Cyber Security
A four steps approach presents the process for connecting and adjusting information from Operational Scenario OpeSce and Vulnerabilities.
. Operational vulnerabilities relate to how organizations do business. Risk-based vulnerability management uses machine learning to extend vulnerability management beyond traditional IT assets incorporating cloud infrastructure IoT devices web. Providing essential information to senior leaders to facilitate decisions.
General Services Administration 3 Verifying all assets hardware and software in the AA boundary. 111 Identifying School Core Functions. Vulnerability management is the process that identifies and evaluates risks of the IT systems which are then removed or remediated.
Risk Management Handbook RMH Chapter 14. STEP 1 Link Operational Scenarios and. PR-VAM-001 Performs assessments of systems and networks within the network environment or enclave and identifies where those.
CIO-IT Security-17-80 Revision 1 Vulnerability Management Process US. Risk Assessment RA 6 Version 10 1. An effective IT asset management ITAM solution can tie together physical and virtual assets and provide management with a complete picture of what where and how assets are being.
Risk takes into account the value of an asset the threats or hazards that potentially impact the asset and the vulnerability of the asset to the threat or security risk rating In the risk analysis. Similarly a single risk scoring can consider two of these or all. The risk to an asset is a level of likelihood of a threat agent initiating a particular threat which exploits a specific vulnerability in the asset causing a certain level of impact or harm.
Vulnerability is defined to be a combination of the attractiveness of a facility as a target and the level of deterrence andor defense provided by the existing countermeasures. A weak process that allows for someone to. 1-4 ASSET VALUE THREATHAZARD VULNERABILITY AND RISK ASSET VALUE THREATHAZARD VULNERABILITY AND RISK 1-5.
InsightVM Rapid7s leading vulnerability risk management solution helps organizations discover devices in hybrid environments assess for vulnerabilities and. The past decade has flooded asset managers with challenges and complicationsfrom escalating cyber-attacks service provider and exchange outages and. Excessive information posted on a website is an operational vulnerability.
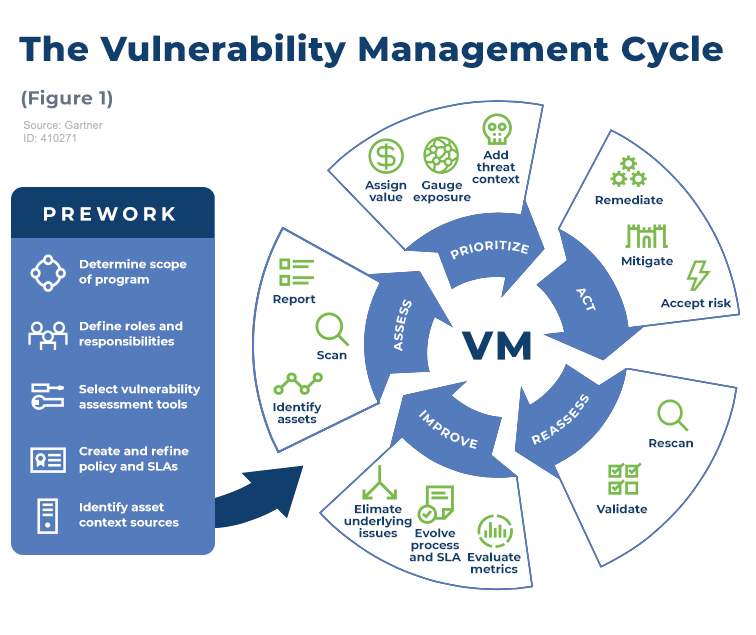
Vulnerability Management Introduction Prework

Introduction To Vulnerability Management Bmc Software Blogs

Deloitte Framework Risk Management Continuity Vulnerability

Isms Process Framework Download Scientific Diagram Framework Process Diagram

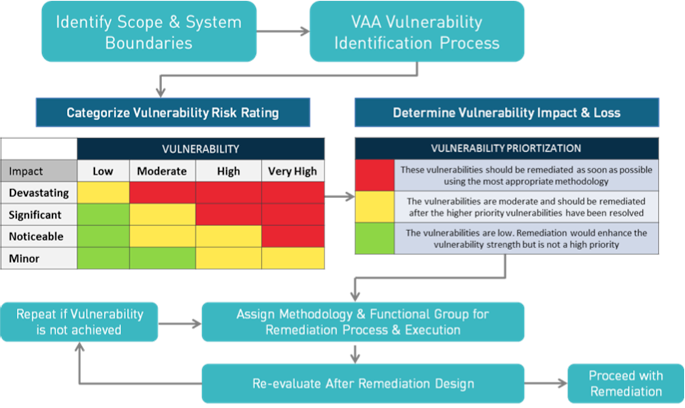
Vulnerability Analysis Assessment Vaa Arms Reliability

Compliance Vigil Risk And Compliance Dashboards Cybersecurity Security Solutions Cyber Security Operational Excellence

Vulnerability Management Services Vulnerability Management Is A Drain On Your Security Team Scans Take Too Long Vulne Vulnerability Management Cyber Security

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs
0 Comments